Write Up : backdoor HTB
By bocahganteng
Register our target IP into /etc/hosts so we can access backdoor.htb (optional)
1. Scanning Phase
➢ Nmap Scanning
2. Exploit Phase
➢ Exploitation port 80
Scanning result which is use Wordpress CMS ,so im decide to use wpsscan to enumerate
We found admin username,and then we must search the password so we can login to CMS dashboard. Iam get wp-config.php using the plugins installed on CMS, but still cant to login for
ssh and login page.
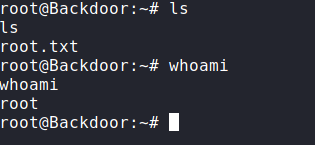
➢ Exploit port 1337
Port 1337 im cannt make sure for what it is,but, that port use for gdb server
https://sourceware.org/gdb/onlinedocs/gdb/Server.html ,after that we search vuln on that
service and found https://www.exploit-db.com/exploits/50539