Introduction with Mobile Penetration Test
Hello, welcome back again with me, Bayu Aji. Sorry I haven't been creating content lately, I've been busy with my work and some homework from school
Introduction with Mobile Penetration Test
Penetration test which a part of cybersecurity especially red team have to a conduct to make sure some apps,services,network,or server work it safety or minimize the vulnerable from cyber attack.Along a time grow up cyber attack surface made big challenge when face the mobile app.Why…? because mobile make activity to effective and efficience to access anything anytime,anyplace,and any condition,soo this benefit from the mobile make a big deal of the threats
Minimizing risk and threats of mobile apps is obligation of everypeople which have access to services.IT Security Department have a biggest part securing,minimazing,made some internal regulatiom.policy and training to other employments so the organization ca be more though.
Mobile App penetration part of a IT Secuirty Department have to conduct to testing app at least coding,logging and activy.To learn the point of testing we can use DIVA ( Damn Insecure and Vuln App).Diva have been create use unsecured coding, so we can learen every module from the DIVA.
DIVA’s module has been setup to every people whos want to learn about mobile app like mobile andro developer,quality assurance,it security and student.
DIVA’s module
at this chance we doing 1st challenge from DIVA which is a Insecure Logging.Log is diary activity from the app,while have been write to a long time from the turn on service to turn off the service.The Diary of log have a crusial information.
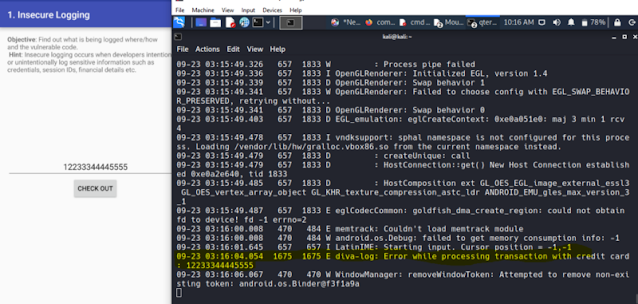
Insecure Log
the challenge is we can capture or seeing whats system doing,like the picture above people who input her/his credit card number and the system read that input after check out is tapping.at this point we can capture while system is reading the input of the user using adb logcat,at this point attacker can see have a cridentials information,which can be utilized for selfish or anything.
Why can be happen ? and how to minimaze ???
like a people whos write her/his diary,mobile doing that too,mobile have place to write some general log,seems picture above when im capture log the mobile.
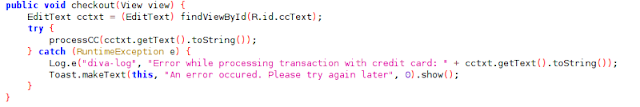
Insecure Logging Code
from the code have been writed log.e(“diva-log”, Error while …. )); so when error or unaccepeting string the code will be announced what kind of error and the string where is an input will be show too,example we have input 12233344445555 to credit card input field,when facing the error ,wrong or unaccepting value,the code will be write “ Error while processing transaction with credit card”and the code will append the string was were inputed,so the finally is ““ Error while processing transaction with credit card :
122333444455555”,the string which input was got an error should be doesn’t showing, to made it safety just show wan kind error but dont specificly like username is wrong or password is wrong, but make it more generally ,this made more hard to predict which wrong and right credentials.We can imagine how about this ,where we didn’t know was we were got some sniff and we use our creditcard, and we fall in to hole.
OWASP recommends the following measures according to the risk of the data stored or processed by the application:
· All login, access control, and server-side input validation errors should be logged with sufficient user context to identify suspicious or malicious accounts. Logs should be retained for a period of time that allows delayed forensic analysis.
· Ensure that logs are created in a format that can be easily used by central log management tools.
· High-value transactions should have an audit trail with integrity controls to prevent manipulation or deletion.
· Effective monitoring and alerting should be established so that suspicious activities can be detected and responded to in a timely manner.
· A response and recovery plan shall be established for incidents, such as NIST 800–61 rev. 2.
Reference
1. https://medium.com/@javan.rasokat/owasp-appsensor-logging-and-monitoring-2518712ee0fe
2. https://github.com/payatu/diva-android
3. https://owasp.org/www-project-top-ten/2017/A10_2017-Insufficient_Logging%2526Monitoring
4. https://cheatsheetseries.owasp.org/cheatsheets/Logging_Cheat_Sheet.html
5. https://owasp.org/www-project-proactive-controls/v3/en/c9-security-logging
6. https://owasp.org/www-project-mobile-top-10/2016-risks/m2-insecure-data-storage
7. https://securitygrind.com/mobile-risks-m2-insecure-data-storage/