OSINT Open Source Intelligence Fundamental
Hello, come back with me Bayu Aji, sorry if I rarely actively write articles due to many deadlines that must be completed, so while I have time this time I will discuss about OSINT (Open Source Intelligence)
I thank Seth from pcwdld.org for contacting and reminding me to write an article about OSINT and provide OSINT resources to add and I will keep that promise. If you attended a seminar from TegalSec entitled "How Secure and Valuable Your Data" presented by Bayu Aji, Danang Avan, Hasyim Asyari, surely you are already familiar with OSINT, but don't worry for those of you who don't attend this seminar, I will explain again about OSINT but here I will not describe it in full and in detail because this technique is quite dangerous for example, someone can find your information easily, doxing, stalker and others. I as a writer here do not teach you bad things, no way use this technique properly and correctly. Take advantage of your knowledge for good, don't abuse it, ok, now it's time to get back to the topic, then what is OSINT?
What is OSINT?
Ok, now I will explain what OSINT is. OSINT is a technique of collecting data, analyzing data from open sources (Open Source) For example from Google, Bing, Yandex, Baidu, Social Media you can do information gathering and recon, footprinting by utilizing open source data. After you get that information then what is your purpose for doing it? For example, for profiling, hacking, analyzing threat actors, for fun and others, there are many motives or intentions that you can do.
Things OSINT can do
OSINT, can do anything, not only profiling but you can analyze cases such as analyzing threat actors, malware and others, many things can be done by OSINT I personally use OSINT for profiling purposes, analyzing cases, looking for original sources, documents and others. I did this not to be illegal but for a specific purpose. Ok I will explain some cases that can be done by OSINT including:
- Profiling
- Doxing
- Looking for facts
- Searching for documents
- Analyze cases
- tracking
- Hacking
- etc
Who uses OSINT?
Ok, who is OSINT for? Hoho this is good material. OSINT is often used by researchers. journalists, officials and the general public, make no mistake. General people can also use this technique with certain motives but what I often encounter, especially for general people (not practitioners) Only knowing the basics, for example what is known is social media ignorance, looking for the core username is only profiling or can be said to be stupid, actually there is so much that can be used from this technique. For this reason, OSINT is often used by researchers, the following are for whom OSINT is used, including the following:
- Apparatus
- Government
- Company
- Hackers
- Journalist
- common people
OSINT branch
OSINT has branches including the following:
SOCMINT can be defined as the techniques, technologies and tools that enable the collection and analysis of information from social media platforms. SOCMINT can be leveraged by governmental or non-state actors, such as private intelligence agencies or marketing firms, to gain knowledge about specific individuals, groups, events, or a number of other targets.
SOCMINT is not as easy as OSINT because there is a belief, especially by users and privacy advocates, that there is some expectation of privacy when using social media platforms. While OSINT researchers may disagree with these expectations, there are other aspects of SOCMINT that are worth considering.
- Forums
- Youtube
- Groups
The information found on social media platforms is not limited to text and images. It may also include contextual information about the piece of content. Metadata can include the location tagged in a post, the time the post was created, or even the type of device used to take the picture
HUMINT is information collected, provided by human sources (Direct) investigations collected through interpersonal contacts, gathering more technical information such as Signal Intelligence (SIGINT) SIGINT is intelligence that we gather by listening to other people's conversations, while HUMINT is intelligence collected by humans in the field itself (Interaction), Imagery Intelligence (IMINT) and Measurement and Signature Intelligence (MASINT).
Techniques in HUMIT:
- Documents, Photos secretly (Incognito)
- Direct contact (Interaction)
- Relations with the government
- HUMINT can infiltrate groups or agencies (Incognito)
- Target profiling (Talent Spotting)
- Leverage the information they know about someone, to direct them to a specific course of action
- The skill known as Emotional Intelligence
- Understand body language, facial micro-expressions and other small, barely perceptible clues to the target's mindset
- Being someone else takes on a personality or role outside of their usual self
HUMINT collects and reports information from friends, civilians, refugees, and local residents as well (Persons close or related)
HUMINT's traits:
- Patience
- Precautions
- Credibility/Integrity
- Objectivity
- Self control / Self discipline
- Adaptability and flexibility
- Perseverance
HUMINT is not just anyone, HUMINT consists of intelligence agents such as state officials and others, a HUMINT person can be financed by certain agencies and tends to be difficult for the general public to do. HUMINT is often involved with government affairs
I can't talk about this in detail. Because this is very complicated to explain and can be used by irresponsible people, for that I will share only the basics. The rest you look for yourself in the open information in this article, I don't want to be the material for crime
You can learn more about the OSINT branch with the keywords I have provided above, you can explore through open sources, I will provide the OSINT handbook and cheat sheet for you, the link I will provide below
OSINT technique
Ookok, it's not enough if you don't discuss the OSINT technique, I will explain the most basic OSINT technique if you want to learn more you can read the handbook that I have made. The link I will provide below, this is the most basic technique in OSINT for information gathering and footprinting, including the following:
- Dorking
- Reverse Similar
- Metadata dan Hash (File Analysis)
- Menganalisis
OSINT tools
If you can't code (Programming) Don't worry because OSINT has minimal coding but it's better if you understand what coding is for, bro? Yess if you can program you can create your own tools and exploits if needed because some OSINT cases require skills to analyze, hack, exploit and understand a flow what you are working on examples of malware, exploits of threat actors (Digital Forensic) And other things. Ok now I will describe OSINT tools that are often used and powerful
- Maltego
- Spiderfoot
- Exiftool
- Recon-ng
- OSINT Framework
- Get Contact
- Etc
Here is our list of the ten best OSINT tools:
1. Recon-ng – EDITOR'S CHOICE This is a free tool from an open source project that enables the user to gather, collate, and correlate information for open source data sources. This system runs on Docker, so it is operating system independent and can be deployed on Windows, Linux, macOS, or Unix.
2. Shodan A search engine that indexes everything on the internet other than websites, such as IoT devices, smart devices, vehicles, and routers. This is an online service and requires a subscription for access.
3. Maltego This tool has many uses; it finds connections between data instances and creates a map. It will help you to find out who knows who by searching through social media profiles. Available in free and paid versions, this package installs on Windows, macOS, Linux.
4. theHarvester This tool searches through a range of data sources on the internet to collect information on a given person, system, company, or event. Available for Linux.
5. Recorded Future This is a cloud platform that gives access to threat intelligence sources and allows the user to extract possible hacker activity.
6. Metagoofil This is a free passive reconnaissance tool that uses Google to locate files that have metadata related to a target, downloads them, and then indexes them for the relevant information. Runs on Linux.
7. Searchcode A free, web-based search tool that identifies security exploits in publicly available programs.
8. GHDB The Google Hacking Database is a free online searchable database of tricky Google search strings that can extract important information about a target system with a Google search.
9. SpiderFoot A free tool that performs “fingerprinting” on a topic by linking together different discoveries about a given target. Runs on Windows and Linux.
10. OSINT Framework A free online system that presents a collection of investigative tools that link together to discover and present information about a target.
We take it for granted, but today we have the kind of technology that intelligence agencies, two to three decades ago, would have only dreamt of.
Bonus tips
Cryptocurrency investigation
I will give you a bonus, regarding cryptocurrency investigation. Talking about cryptocurrencies is a complicated thing, the article is anonymous, although transactions can be seen publicly and account statuses such as balance amounts can be seen, but cryptocurrencies are difficult to track. complicated, someone can change their address with a certain deadline, for example, 1 day, 1 hour and so on. If you know the electrum wallet, one of the wallet platforms that you can use, I think this is useful for you in making transactions
Cryptocurrency is often used for criminals such as scams, fraud, malware. Cryptocurrency can be tracked by identifying transaction activities, profiling addresses (Complicated) and others, someone who knows cryptocurrency usually they will not share addresses on social media and the public, and this exchange is without KYC (Know your customer) but many platforms must provide KYC but this can be avoided with fake KYC, for example you can pay people, data collection with the lure this is a way for criminals, a lot can be done to commit fraud, please think for yourself hahahaha
Platform :
- Blockchain.com
- Flashpoint
- Intel471
- Tatum
- Ciphertrace
- Bitcoin cash
- Bitcoin abuse
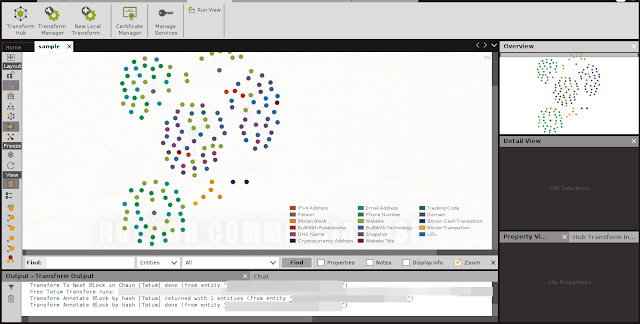
How to use the platform? You can use Maltego to use it, the method is quite easy you just search for what transform to use then you can install it on your machine, it is important to understand that some Maltego transforms are paid you need to subscribe if you have more budget you can buy the enterprise version of Maltego or subscribe to transform. If you often use this tool and work with this tool, it never hurts to spend a budget to buy and make your work easier
Investigation
How to track and graph a comprehensive Bitcoin transaction
Step by step process to find important Bitcoin addresses
Case Study: Analyzing a large Bitcoin chart
Investigation
How to visualize activity on the Ethereum network
Working with and importing external data sources into Maltego
Case Study: Analyzing a huge Ethereum chart
Challenges in OSINT?
The challenge in OSINT is that there are many things, one of which is if you are currently investigating a private target that is closed it will be very difficult to do profiling, difficult does not mean you can't do various ways, for example doing social e to the target. Social e is not easy, what is imagined requires strategy and a long time to trap the target, for example you can do social e then you know what he is looking for and likes or you can make a program that contains a logger you can enter it into the tools , files and others when the target runs and opens then you will get access. Or you can disguise yourself and do HUMINT to the target, look for close people, neighbors to get target information, as for some other challenges from OSINT including the following
- Amount
Social media platforms like Facebook and Twitter have billions of users. With so much data available, it can be difficult to find relevant information
- Identification
Many platforms operate with the aim of maintaining the confidentiality of their users' identities (Respect privacy), this is a challenge for investigators. In addition, the increasing prevalence of fake accounts (Sockpuppet) on these platforms can make it very difficult to know which data is accurate, available and useful.
That is one of the challenges of OSINT or investigators, a good investigator is those who can be patient and analyze further to validate the truth. OSINT can't be fast, it takes time even though there are adequate tools and gadgets that can't guarantee a faster process, it all depends on your strategy and what your target is
Important points in conducting an investigation:
- Name
Name is the identity of a person and social media account Facebook, Myspace, or LinkedIn. However, it is also the first personal identifier that people will avoid using or revealing if they don't want to be found
- Email Address and Number
This is a great starting point as it is usually only shared between accounts, and thus, individuals, who are somehow connected. So, if two accounts on different platforms share the same phone number or email address, it means there is a link between them. The problem with these data points is that they are usually not easy to find (Skype is an exception) and don't show up on interesting people's profiles
- Picture
Profile image Performing an image search (Reverse image) of images found on your profile may lead you to accounts operated by the same person. However, it could also be that two different people think that the specified image will look good on their profile
Searching for an account with an image as the point of departure is also much more difficult because you have to rely on image search engines like Yandex, PimEyes, which are not usually a feature supported by social media platforms.
- Address and bio
Addresses and biographies are probably the most difficult to exploit. Rarely will an individual reveal their physical address on social media. Online information-gathering platforms such as Pipl are more likely to allow investigators to move away from such information. On the other hand, biographies should always be viewed with caution because some individuals link their social media accounts using their bios, you can do metadata investigations, do social e, embed logger programs and so on.
Why are criminals so hard to catch?
A high-class criminal (High level) Very understand the ins and outs of investigators. Good criminals are those who do not expose anything on social media and the general public, they will be closed without revealing their crimes, for example, their daily Facebook profile only uploads memes, changes profiles, and so on but you don't know that he is. criminal. But criminals can be exposed, it just takes time to remember an investigator plays in a group of many people and is cunning, you are alone and only a few people, imagine you are fighting 2 vs 20 people then obviously 20 people will win. Investigators such as agencies play gangs (Groups) as well as sophisticated gadgets such as glasses, lighters can record, pens can record, power banks and wallets can record, lights can record, planted earphones and others. I'm not lying or inspired from the movie but it exists in the real world like a car specially designed for disguise like an old, ramshackle car but there's something in it that you don't know, what criminals usually do is do sockpuppet, disguise, remove traces every time he commits a crime, for example, organically making sockpuppets, exchanging files through onion shares, locking messages and not tending to be exposed on social media such as Twitter, Facebook. Even the best criminals are those who don't expose their emails, photos, etc
An investigator can disguise various things, such as being a prostitute, being a teacher, student, reporter and others. An investigator is difficult to identify, for example an investigator does not have to be well-built, disguised as a criminal, joins a criminal gang and others, you cannot find the investigator parameters, then the best step for criminals is usually they will validate the person first , find out in depth, commit crimes in a neat and structured way, I'm not here to teach you bad things but analyze criminals
Prevent OSINT
Once you learn what OSINT is. Then how to avoid or reduce from OSINT? Actually, if you have used the internet and social media, then your privacy has been shared, for example your ip address, hostname, your data, your searches, the posts you publish and others, but it is undeniable that you can be anonymous or hide your identity, in various ways. among them as follows:
- Hide IP (Tor, p2p, vpn)
- Sock puppets
- Tails OS
- Dont share personal ident
- Jangan berbuat aneh aneh dan hal bodoh
- Delete metadata
- Add encryption message (pgp)
- 2FA account social media
- Etc
Conclusion
Ok, now I conclude that OSINT is a useful technique for you to conduct investigations, profiling, information gathering and other things. But OSINT can be a crime, for example, doxing is not allowed, each technique must have advantages and disadvantages, if you want to learn more, you can learn in the handbook and cheat sheet that I have given, basically if you want to be safe then the best way The thing is don't use the internet, nowadays we can't be separated from the internet, so the best way is don't reveal your personal identity, don't play social media, protect your own data, like keeping your crush so you don't get cheated on. You NTR uuuuuhh its hurt bous
Useful link
Download handbook : https://forum.seccodeid.com/archives
Site : https://forum.seccodeid.com/archives
Telegram : https://t.me/seccodeid/87
OSINT cheat sheet : https://github.com/Jieyab89/OSINT-Cheat-sheet-
https://www.pcwdld.com/osint-tools-and-software#wbounce-modal
https://blog.tegalsec.org/osint-tutorial-maltego-open-source-intelligence-free-handbook/